How EV Charger Manufacturers Can Build Secure, Reliable Connected Products
Learn how EV charger manufacturers can bring connected products to market faster, adhere to strict security standards that meet regulatory requirements, future-proof their designs, and win over skeptical consumers.
This article was first published on
www.particle.ioNew legislation in the U.K., U.S., and beyond will include requirements for electric vehicle chargers to be connected to the Internet. This legislation will bring numerous benefits to the EV ecosystem, along with the risks that come with connectivity.
Beyond simply creating physically safe and tamper-proof EV chargers, today's manufacturers must consider the cybersecurity practices around the devices, firmware, connectivity, and application ecosystems that surround their products.
As the private and public EV charging network grows, so have reports of malicious actors hacking the system. In fact, Ars Technica reported that these malicious actors were responsible for attacking power grids across Europe, which led to outages, identity theft, and stolen payments. Meanwhile, when U.K. cybersecurity company Pen Test Partners tested several popular EV charger brands last year, it found major vulnerabilities that put infrastructure, sensitive data, and user safety at risk.
These attacks—and the legislation that is aiming to reduce them—highlight an uncomfortable truth for EV charger manufacturers: Getting to market quickly cannot come at the expense of building secure, reliable products.
In fact, achieving wide EV charger adoption and creating competitive differentiation will in large part come down to which manufacturers can ensure system owners' safety.
In this article, we’ll discuss how EV charger manufacturers can bring connected products to market faster, adhere to strict security standards that meet regulatory requirements, future-proof their designs, and win over skeptical consumers.
Summary
- New U.K. regulations will require EV chargers to have built-in Internet-connectivity, with security as a focus.
- One of the most important parts of this legislation is the Secure Boot requirement, wherein a device's firmware and operating system are authenticated against a known secure key—placed on the device at the time of manufacture—whenever the device is booted.
- EV chargers will need to be physically tamper-proof and equipped with the ability to detect energy theft. From a cybersecurity perspective, EV charger manufacturers must include features such as firmware signing capabilities, input validation, abstracted APIs, and over-the-air update capabilities.
- When updating older product lines or launching new ones, EV charger manufacturers should look for a connectivity and IoT partner that provides critical security features like Secure Boot, easy OTA updates, an operating system with a minimal attack surface, and a secure data pipeline.
- Particle’s new enterprise Wi-Fi solutions, the Photon 2 and P2, provide everything EV charging manufacturers need to swiftly build connectivity into their products in a manner that exceeds all new security requirements.
Changing U.K. Regulations for EV Chargers
Because every EV charging manufacturer operates within the context of its markets’ regulatory frameworks, it’s critical to understand how these frameworks are changing and what impact these changes will have on the requirements to which any new EV charging product must adhere.
EV Chargers Get Smart
EV chargers in the U.K. are set to graduate from purely physical to connected “smart” products thanks to The Electric Vehicles (Smart Charge Points) Regulations 2021 legislation that took effect on June 30, 2022.
As stated in the regulations, all new EV charge points—whether privately owned or public—must include connectivity features that make it easier for charge point owners to efficiently manage their energy use.
At a high level, that means:
- All new EV chargers in the U.K. will connect to the Internet and have the ability to monitor usage. For electricity suppliers, this means greater visibility into demands on the smart grid, which will allow for better capacity management and infrastructure investment. For EV owners, this translates to having more control over chargers via a smartphone app.
- New home chargers must be preset to charge during off-peak hours, thereby reducing the load on the grid and saving the system owner money.
- New home chargers will automatically stagger charging sessions across entire fleets to ensure every device is not charging at the same time.
- All smart EV chargers must be compliant with GDPR and other data privacy and security laws that require user data encryption and give system owners more control over what data gets stored.
Although many EV charging manufacturers have already started building connected solutions, others are scrambling to incorporate this functionality before the regulations take effect. For many, the new security requirements are top of mind.
A Focus on Security: The Secure Boot Requirement
While most of the new security regulations cover standard industry best practices, the requirement for validating software updates via Secure Boot is a major change from previous EV charger security regulations. By January 1, 2023, all EV chargers will have to support an enhanced security scheme that includes Secure Boot.
Here’s the relevant section:
3.—(1) A relevant charge point must incorporate software which is able to be securely updated.
(2) In sub-paragraph (1), securely updated means updated using adequate cryptographic measures to protect against a cyber-attack.
(3) A relevant charge point must be configured so that— (a) it checks, when it is first set up by the owner, and periodically thereafter, whether there are security updates available for it; (b) it verifies the authenticity and integrity of each prospective software update by reference to both the data’s origin and its contents and only applies the update if the authenticity and integrity of the software have been validated;
(4) A relevant charge point must be configured so that— (a) it verifies, via secure boot mechanisms, that its software has not been altered other than in accordance with a software update which has been validated in accordance with sub-paragraph (3)(b) above; (b) if an unauthorised change to the software is detected, it notifies the owner and does not connect to a communications network other than for the purposes of this notification.
What Is Secure Boot?
If someone has physical access to a device, they can compromise it. Secure Boot is designed to prevent this.
As described previously, “Secure Boot” refers to the process of authenticating a device’s firmware and operating system against a known secure key placed on the device at the time of manufacture. This authentication occurs every time the device is booted in order to validate that the firmware or code being loaded was placed there by whoever produced it.
Thanks to Secure Boot, any hacker able to gain physical access to a device embedded in an EV charger would be unable to boot their own modified firmware or bootloader, as this wouldn’t cryptographically match the secure key implemented by the manufacturer.
In the context of individual EV chargers or charger networks, Secure Boot is a vital security practice that prevents negative outcomes such as:
- Energy theft
- Impeded charging
- Stolen customer or business data
- Access to system owners’ home Wi-Fi networks
- Physical equipment and infrastructural damage due to malicious or improper usage
Meeting Compliance Requirements Without Hindering Speed to Market
In any competitive market, timely shipping is critical, and the EV charger market is no exception. Because system owners rarely opt to swap one charger for another post-installation, first movers have an advantage, yet engineering any solution to the problem of building secure and reliable EV chargers—whether in-house or with a platform partner—can add months or even years to the product development cycle.
Protecting Your EV Chargers From Security Threats
Before we get into how you can build more secure EV chargers, it’s important to understand what it means for a charger to be secure—and, perhaps more importantly, what makes a charger vulnerable.
What Does It Mean for an EV Charger to Be ‘Secure’?
A secure EV charger must meet high standards for both physical and digital security.
Physically, any EV charger should be:
- Tamper-proof, with the goal of preventing physical access to devices or exposure to high voltage. The new legislation also requires EV chargers to have secure tamper-detection capabilities
- Able to detect energy theft and then automatically shut down after alerting the manufacturer and system owner.
From a cybersecurity perspective, EV chargers should include the following, at a minimum:
- Firmware signing capabilities to prevent new, unauthorized firmware from being pushed remotely or by a physical attacker—in other words, Secure Boot.
- Input validation that determines whether a value entered into the software or application is within an expected range.
- Abstracted APIs that make account takeovers difficult, if not impossible.
- OTA update capabilities that allow manufacturers to securely push software updates and patches without relying on the customer or dealer/distributor.
Common EV Charger Attack Vectors
In addition to knowing what makes an EV charger safe, it’s worth understanding the common attack vectors to which EV chargers can be vulnerable. These include unsafe devices, port scans, unpatchable security issues, and application and ecosystem vulnerabilities, which we’ll explore in more detail next.
Unsafe Devices
According to the aforementioned Pen Test Partners, EV chargers built using Raspberry Pi compute modules that typically run a version of embedded Linux are at risk of “easy extraction of all stored data, including credentials and the Wi-Fi Pre-Shared Key.”
In general, hobbyist modules like Raspberry Pi are cheap and easy to use, but they fall short in terms of meeting the security standards required of enterprises creating products that handle user data and connect to critical infrastructure.
Still, EV charging manufacturers seeking a fast way to get a connected solution to market often load their code onto Raspberry Pi and put it into their existing hardware without clearing away any extraneous code that doesn’t serve their use case. It’s this extra code that increases the attack surface on the device, ultimately increasing vulnerability.
Port Scans
Unsafe devices with bloated firmware and embedded Linux are typically more likely to show up in port scans—a common tactic that allows bad actors and Internet of Things botnets to find open ports on a device and determine information such as which services are running, which users own specific services, and which ports are sending and receiving data.
For devices connected to Wi-Fi networks and running embedded Linux, default credentials can frequently be leveraged to access the services that show up on port scans. Typically, a malicious actor conducts a port scan, determines that the secure shell managing the device is enabled, then fires random default credentials at it. If successful, they’ll gain access to the Linux shell.
If the device is running an outdated version of vulnerable software such as the Linux kernel, even a hacker who gains access to the shell as a low-privilege user can exploit local permissions vulnerabilities to escalate their way to root-level access, paving the way for them to control the charger or load their own firmware.
While port scans can be executed remotely, anyone with physical access to the device embedded in an EV charger can cause damage via debug ports.
Unpatchable Security Issues
One of the biggest issues with IoT devices in general is that they tend to be harder to keep up to date with the latest security patches and fixes. In many cases, the devices are built, shipped, and left in the field for years—and because traveling to them to manually run updates is expensive and time-consuming, their vulnerabilities are often left unpatched indefinitely.
Not having the ability to receive OTA updates is a security flaw in the sense that discovered vulnerabilities can be exploited easily while fixes are slow. Requiring end users or technicians to physically load updates onto a device is a surefire way to ensure the firmware stays open to attack.
Application and Ecosystem Vulnerabilities
Even if an EV charger has top-of-the-line device security, poorly designed web applications can be an easy attack vector. After all, if fleet management solutions or user-facing web apps haven’t been tested against rigorous security checks, they’ll leave chargers vulnerable.
In fact, Pen Test Partners found API authorization issues and unauthenticated GraphQL endpoints in several EV charger platforms. These vulnerabilities allow for full account takeovers, easy access to user data, and complete control over chargers’ behavior.
Building Secure EV Chargers While Shipping Product on Time
So, how can you avoid the aforementioned common security flaws, stay compliant with stricter regulations, and deliver a reliable product customers want to buy?
In this section, we’ll discuss how building connected EV chargers with Particle can provide a secure foundation for connectivity while helping you get to market faster.
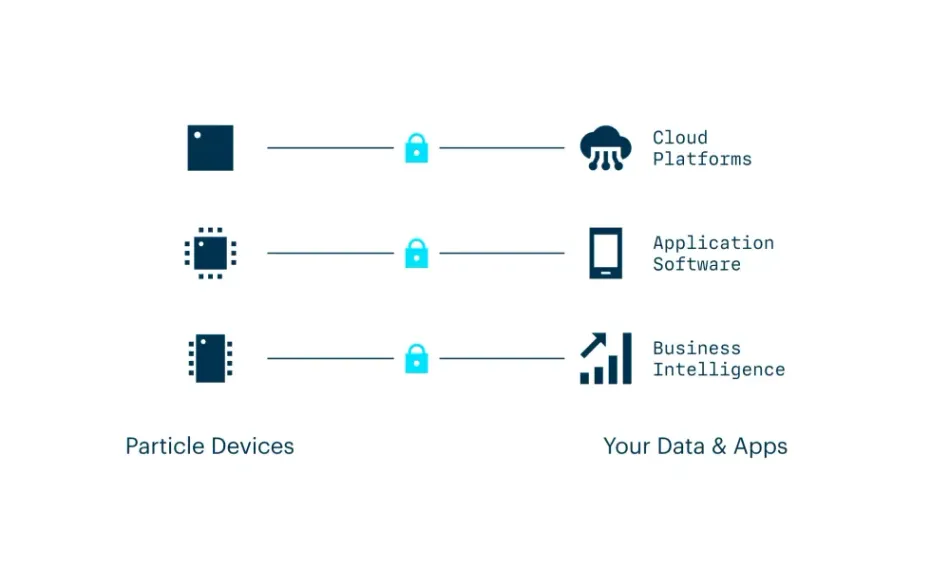
An Integrated IoT Platform-as-a-Service
The platform you use to build connectivity into your EV chargers has a major influence on how secure you can credibly claim to be, as homegrown IoT projects often use a mishmash of integrated point solutions and off-the-shelf devices that can lead to security issues. IoT platforms offering devices and connectivity but no cloud backend frequently run into similar problems.
Particle’s IoT Platform-as-a-Service was built to work as a single unified platform that brings everything you need to build a connected product into one place. Instead of trying to make disparate systems “talk to each other”—thereby creating gaps in security—Particle handles devices, software, and connectivity for you.
Secure Enterprise-Grade Wi-Fi Modules for Connected EV Chargers
While cellular connectivity is an option for connected EV chargers, system owners typically need to connect to home or public Wi-Fi networks.
Historically, using Wi-Fi for IoT purposes has yielded numerous challenges associated with end users managing their public or private networks themselves—which, unless they’re security experts, opens up network management vulnerabilities. That’s why Wi-Fi security starts at the device level.
Particle’s latest Wi-Fi devices, the Photon 2 and P2, take our leading security practices above and beyond what regulators in the U.K. and elsewhere require of an EV charger.
Encrypted and Secure Boot-Ready, Right off the Production Line
Whether from platform providers or for prototyping/hobbyist use, many off-the-shelf modules are sourced from third parties—in other words, it can be hard to ascertain whether devices are signed before they’re sold.
Every Particle device is signed with an individual key at the time of manufacture that ensures compliance with all Secure Boot requirements for EV chargers, and the Photon 2 and P2 are no exception. Our Secure Boot mechanism is backed by Fortanix HSM, which is used in highly secure communications devices for enterprise and government use, and the Photon 2 and P2 are manufactured with built-in encrypted flash and ARM TrustZone technology.
Encrypted flash prevents malicious actors from taking chips off the board and reading their contents, as everything will be garbled without the key set at the factory.
ARM TrustZone is a well-known mechanism that provides a layer—or “zone”—of trust between the secure device functions and the operating system. Essentially, the parts of the device that generate cryptographically secure keys and the general user space where you write your firmware are separated by a layer of abstraction, ensuring the parts that require absolute integrity are unable to be manipulated.
Particle Device OS: A Minimalist Embedded IoT Operating System
The entire Particle IoT Platform-as-a-Service is integrated into every device we make. All devices—including the Photon 2 and P2—come pre-flashed with Particle Device OS, our embedded IoT operating system. They are ready to connect to the Particle Cloud as soon as they’re turned on.
Unlike open source operating systems, Particle Device OS eliminates common vulnerabilities that malicious actors use to break into and exploit OSs. Particle Device OS is a key asset in your EV charger’s security arsenal for the following reasons:
Minimal Attack Surface
Open source OSs like embedded Linux expose code that is unnecessary for device functionality, opening up the potential for port scans and the exploitation of other vulnerabilities.
In short, simplicity is security. Particle Device OS has no open ports and leverages only services that are essential to connect to the Particle Cloud. By removing the extra fluff included in most open source OSs, Particle Device OS is secure and ready to use right out of the box.
Abstracted APIs
Particle Device OS abstracts the complex integration among microcontrollers, modems, peripherals, verified libraries, and your application firmware, setting up your product’s physical device to work seamlessly and securely.
Particle Device OS is maintained and released at a regular cadence, representing ongoing improvements, learning, and robust performance for devices distributed to a community of more than 140,000 developers across eight years. To date, more than 115,000 hours (55 EP) have been dedicated to our device OS development, and nearly a dozen engineers regularly execute maintenance and extend functionality.
Long-Term Support Versions
Enterprises building and deploying mission-critical solutions with Particle tend to value reliability over everything else. For those customers, Particle develops and releases long-term support versions of Particle Device OS that deliver consistent behavior and stable performance for device applications over extended periods of time.
These LTS releases for Particle Device OS are independent branches of the operating system that are feature-frozen in time. In other words, they do not receive updates with new features, API changes, or improvements that change device function or standard behavior.
That said, LTS releases are covered by an extended support window to address critical bugs, regressions, security vulnerabilities, and issues that affect our wider enterprise customer community.
OTA Updates
Particle OTA Services lets you push OTA updates with a single line of code or a few clicks, making it simple to add new features, respond to security vulnerabilities, or change product behavior after you’ve shipped.
Our OTA updates are:
Secure All OTA updates between Particle Device OS and Particle Cloud are encrypted—including firmware files—to prevent man-in-the-middle attacks. Every update is verified to ensure all senders are approved device managers.
Context-Aware and Reliable Particle won’t push an OTA update if a Particle device is performing a critical operation. By waiting until it’s safe to push updates, Particle helps you avoid costly interruptions and outages caused by bricked products.
Flexible Single-device OTA functions can be used to rapidly iterate on your prototypes. When you’re ready to scale, Particle OTA Services lets you batch OTA updates to many products at once. Release new firmware, test updates on a subset of your fleet, and push updates whenever you want.
A Secure, Encrypted Data Pipeline and Cloud Solution
From the device cloud side, Particle does integrity checks every time the device firmware boots. If an unexpected input such as a code or version change appears, the Particle Cloud will automatically prevent the firmware from booting and then send an alert to you and our security team.
Here’s what Particle Cloud provides from a security standpoint:
- The modules are bound to your account only, with limited access and 2FA employed for secure access to the cloud management interface. Your devices cannot be moved to another account for OTA reprogramming, and only you can unclaim a device from your account.
- Devices are paired with the cloud platform and reverse-connect to a trusted endpoint used for further connectivity.
- Devices are authenticated as they connect to the cloud using public key cryptography. This process assures that the cloud is what it purports to be and is not rogue.
- Particle Cloud knows what firmware to expect. If that firmware doesn’t show up when the device connects, the cloud will intervene in real time to fix the issue with an update, thereby protecting against firmware modification attacks.
- Particle Cloud doesn’t store event payloads or any proprietary information belonging to you or your customers. Rather, storage is limited to diagnostic data that is only used to ensure devices are performing well and that gets auto-purged regularly.
An Extension of Your Security Team
Particle’s security team is always monitoring devices for unusual or unauthorized behavior—and to ensure everything our customers build is secure, we proactively reach out to partner with customer security teams.
Hiring in-house security experts or expensive consultancies won’t be necessary with Particle because we work as a de facto extension of your team. We’re constantly upgrading our operating systems and software to attain the highest security standards in the industry.
Get Your Secure, High-Performance Particle Wi-Fi Modules Today
Don’t waste valuable time trying to build your own connectivity stack. Particle’s Platform-as-a-Service handles the hard, undifferentiated work of building connectivity into hardware products so you can focus on what does differentiate you.
The Photon 2 and P2 represent the latest in enterprise-grade Wi-Fi solutions for EV chargers and other connected products. They are available to order today and include:
- Best-in-class device security with features like OTP for key management, Secure Boot, crypto accelerator, encrypted flash memory, and ARM TrustZone support, along with Particle’s maintained embedded operating system for encrypted device communication and regular security patches and upgrades
- High performance and functionality utilizing the latest 200 MHz ARM M33 + 20 MHz M23 processor technology
- Low power consumption that enables longer battery life and offers features like extended sleep mode
- Expanded application storage with 512KB onboard SRAM, 4MB PSRAM, and 8MB flash memory
- Advanced peripherals support with multiple combinations of PWM, I2C, SPI, GPIO, UART, and I2S, along with onboard RTC and ADC/DAC
- Backward compatibility with P1 and Photon/Argon to ensure uninterrupted development on the Particle platform; the P2 serves as the drop-in replacement for the P1 (API-compatible and footprint-compatible), while Photon 2 is the drop-in replacement for the Photon (API-compatible) and Argon (API-compatible, footprint-compatible)
- Supply Secure components that help customers using Particle’s new Wi-Fi solutions to continue deploying connected products through the extended silicon shortage crisis
- Pre-integration with the Particle IoT Platform to enable out-of-the-box connectivity, simplified application development, OTA software updates, and more
- Pre-certifications including RoHS, FCC, IC CE, and BQB