Are hackers in your network right now?
No need to worry, AI based cybersecurity can help you!

Is your device/network safe? Source: https://pixabay.com/photos/hacker-hack-anonymous-hacking-5332676/
Regardless of which field of profession you are in, you are most definitely using a smart device connected to the internet on a regular/semi-regular basis. In this day and age, you'd have to be living in the woods to be cut off from the digital mesh that encompasses the world. If you're on a University or Office network, then you're part of a LAN(Local Area Network) that inturn connects to many other such smaller branches and finally back to the internet. But do you know if you're the only person with the access to the contents on your device? Are you sure? Think again!
This article is merely meant to be an introductory tool to get you warmed up about cyberthreats, cybersecurity and how AI based cybersecurity is trying to address this. I am not an expert on all the different branches of cybersecurity, so take this with a grain of salt. In cybersecurity terms, a person with malicious intent trying to access a secure network is called an attacker or more colloquially a hacker. A dummy system that looks and functions similar to the real systems on the network is called a decoy. One such decoy that intends to trap and store the details about the attacker that can be used to traceback his/her identity is called a honeypot. A security tool that tries to prevent any external actor from entering a secure network without proper authentication is called a firewall. Every input-output combination that happens within a computer, causes the computer to send-receive several internal communication signals called system calls. A perfectly objective entity that follows all the mathematical rules of logic is called a rational actor and any influence of the world like relationships, need for materialistic possessions, etc makes the entity's logic imperfect and these imperfections are called biases. A state is the comprehensive description of all relevant details that are needed to make an informed, rational decision about a problem. We will be using these terms throughout this article.
So how do we know if there is an attacker in our network? How do we catch him in the act or better yet, prevent him from entering the network altogether? Attackers are highly skilled actors who have intricate knowledge about internal system/network architecture and often engage in research about the specific network they are trying to enter for several days or even weeks using scouting operations before they even attempt an attack. Also an attack can be performed for any number of reasons ranging from establishing a constant presence within a secure network to damaging/stealing sensitive data. So preventing the attacker from ever entering a network, although would be an ideal scenario, isn't entirely practicable if you think about it. Then can we atleast detect and prevent the attacker before they gain control over the network? For that we first have to learn about the different types of possible attacks that are common in a network. These are explained more comprehensively in this article published by cisco so I'm just going to give you a simple one line idea of some important ones:
- Malware attack - Installs malicious software on your computer that can later be used as an access point.
- Phishing - Deceiving the end user by using a platform that looks like a known, trustworthy source to gain access.
- Man-in-the-Middle - When the attacker eavesdrops on a secure communication line between two parties to gain resources.
- Denial of Service - When the attacker floods the network with rubbish signals to use up the bandwidth otherwise needed by the end user.
- SQL injection - Using malicious code to exploit vulnerabilities in the network and gain access to restricted information.
So how do we detect each of these attacks? The most straightforward way would be to constantly monitor the resources used within the network and map it back to the kind of attack that would need that unique set of resources. This is where we can look at system calls. A system calls log would give us a frozen in time screenshot of all the processes that were actively communicating at the time of logging. By using pattern recognition based on years of research done in the field, we can determine the kind of and the level of attack that's currently underway. But is it really that simple? No. Firstly, millions of system calls happen every minute in a single computer, let alone on a network of computers, so logging them and parsing them is no easy task. Secondly, storing such huge log files and doing pattern recognition on a humongous clutter of data is extremely complicated. So how can we do it? This is where an AI can help.
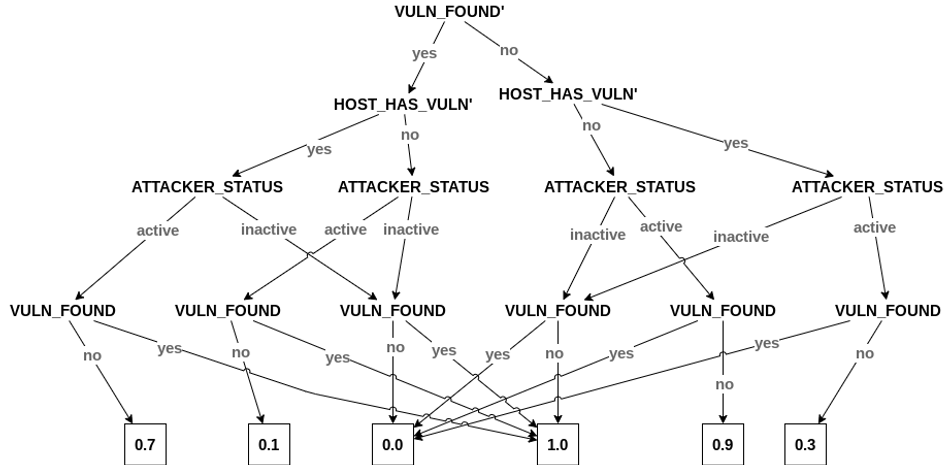
Artificial Intelligence algorithms have been trying to solve problems in all domains for the past few decades now and they've clearly outperformed and outsmarted any single human actor. Additionally, AI algorithms are designed to model and learn from copious data without any human intervention or having to explicitly program the behavior. Since I am not an expert on all the methods currently at the cutting edge of cybersecurity, I will stick to what researchers at THINC Lab are trying to implement. At THINC Lab, we use a tool that's quite popular in classical AI called the Partially Observable Markov Decision Process(POMDP). Without going into the gory details of what that means, it is a tool that helps create a recursive model of reasoning. It tries to model the decision making of the attacker(s) for every counter action that the security software performs to cripple them. This way it can figure out the most optimal action to perform at any given timestep and environment state.
In order to feed the details of the state into the POMDP to make a rational decision, we need to do the datamining of system logs that I mentioned earlier. For this, we use a Convolutional Neural Network to learn the pattern and give us key features about the statespace. Following this, we can use decoys and honeypots to either mislead the attacker into thinking he won or give up less sensitive data while prioritizing protecting the most sensitive files. After testing on simulated attacks, this tool is now ready to be tested on more complex platforms. Eventually we intend to release a commercial version that can be installed just like an antivirus software and used seamlessly on any device.
One caveat with this tool is that POMDPs in its current form can only model fully rational actors which means it assumes that the human attacker always performs the most optimal action. This is not true. Humans are sub-optimal agents who are bound to have biases influencing their decisions. This is the current research topic at THINC lab. We are trying to make the decision making more realistic by trying to model the kind of biases an attacker can have based on the actions he has performed so far. That ends the short tour on cyberthreats, cyber security and AI based cybersecurity models THINC lab is working on. If you want to learn more about what we do, check out our website! I hope you are walking out of this one level more aware than you came in. Thanks for taking this trip on my train of thought!