How cutting-edge microcontrollers build security from the ground up
Alif Semiconductor’s™ microcontrollers meet the market need for low-power, AI-enabled embedded solutions with unmatched levels of multi-layered security, and a fully integrated secure element.
This is the second article in a 3-part series that explains the current state of IoT security and introduces cutting-edge, highly secure MCUs from Alif SemiconductorTM.
Embedded processors are on the rise, getting smaller and smarter. But as more functions are embedded in smaller device footprints, security concerns are increasing. In this article, we will dive into the rising security threats and how new processor solutions are ensuring multiple layers of security for embedded systems. An excellent example of this are the latest products from Alif Semiconductor.
With increasing functionalities, power efficiency, and scalable performance, embedded processors are entering almost every market. You can find them in the automotive, industrial, medical, consumer electronics, and IoT sectors. Estimates show that the embedded processor market is set to grow from USD 21.8 billion in 2021 to USD 44 billion by 2030 at a CAGR of about 8.2%[1]. In other words, the number of embedded processors in the market is expected to double in almost nine years.
However, growth of this magnitude is accompanied by an increase in security threats. For instance, one in every five industrial control systems today faces critical security issues[2]. Embedded systems are often required to store, access, or communicate data of a sensitive nature, making security a serious concern. That is why security must become a priority for embedded systems at every stage of their lifecycle. Such security can provide mechanisms to protect an embedded system from malicious access and unauthorized usage.
Security vulnerabilities in embedded systems necessitate security measures
Security threats can emerge from both software and hardware vulnerabilities. Network-based attacks take advantage of such vulnerabilities to access and take over a device’s processor. The most common are buffer overflow attacks, code injection, and control-flow hijacking.
As we explained in our previous article, embedded security is a partnership between hardware and software. Since the software component is created by human engineers, it is inherently imperfect by nature. Holes in the written code can turn into exploitable bugs of which attackers and threat actors can take advantage. That’s where hardware security comes into play.
Hardware security helps fend off potential threats from happening at both the device and network level. This is characterized by multiple layers of security that enable inherent protection against malware attacks. By providing a root of trust (RoT), and encryption and decryption capabilities, hardware technologies like system-on-a-chip (SoC) can and should maintain the integrity and provenance of a device.
Here are five hardware security measures for embedded processors:
1. Root of trust (RoT)
As its name implies, a RoT is the trusted basis for all secure computing operations. This trust comes from its purposeful security that includes keys for secure boot and cryptographic functions. Implementing a RoT in hardware takes the shape of a stand-alone security module or a built-in security module in a processor, or SoC.
A hardware RoT is established during manufacturing, where a secret key is embedded in a device’s memory to assume the role of the RoT. Once certified by a public key infrastructure (PKI), this key can fundamentally help developers build secure and trusted communications between devices.
A RoT can be either fixed-function or programmable.
- A fixed-function RoT is a finite state machine (FSM) that performs specific functions appropriate for IoT devices, including key management, data encryption, and certificate validation.
- A programmable RoT is established around a CPU that can execute the functions of an FSM with further adaptability and functionality. It can face new attack vectors by running new cryptographic algorithms. It can provide layered security, isolated implementation, and anti-tamper capabilities.
2. Secure boot
Secure boot is a security standard that helps your device boot safely and protects it from any unauthorized software. It utilizes the public key signature provided by the trust anchor and ensures there is no tampering with the software by validating the boot image using the public key.
A public key signature is to digital communications what wax sealing is to historic official documents. It secures whatever information is inside. In this case, it helps establish the provenance of the primary software and its updates.
In case of time-sensitive boot requirements, accelerated boot code validation might be needed. That’s where symmetric keys come into play. A symmetric key can help speed up the verification process and approve the integrity of the software. However, it is a secret key known only to the device, as opposed to the public key.
3. Unique device identity
To establish meaningful communications, devices should have unique identities that are distinguishable and verifiable. Two main approaches to ensuring unique device identity are key injection and using a physical unclonable function (PUF).
- Using key injection: This is where a key - or a cryptographically verifiable identity - is generated in a separate system and securely made accessible to the device. Key injection is a commonly used identification process.
- Using a physical unclonable function (PUF): A PUF serves as a digital fingerprint of the device by showing a physically unique hardware characteristic that can help identify the device.
4. Trusted execution environment (TEE) or hardware security zone
A TEE is an isolated security zone enforced by the device hardware that allows for establishing a root of trust (RoT). This zone is built into the processor and enables security-sensitive processing to take place within the embedded system.
The most popular mode of security for TEEs is ARM TrustZone. It is a system-wide security approach that separates the device resources between the so-called “normal world” and the “secure world”. Security can be further enhanced beyond TrustZone through additional layers of security, as we will see in Alif Semiconductor’s embedded processors below.
Apart from that, a TEE can be run on an isolated CPU core that serves as a “security co-processor” to the main SoC. This isolation establishes a secure execution environment for sensitive processing.
5. Trusted platform module (TPM)
A TPM is hardware that is dedicated to ensuring the security of the device. It is a microcontroller that generates, stores, and uses internal cryptographic keys, encrypts sensitive information in the memory, and establishes the integrity of the system throughout the boot process. It also stores measurements that help with authentication and attestation to ensure trustworthiness.
Multi-layer security with Alif Semiconductor’s highly scalable embedded processors
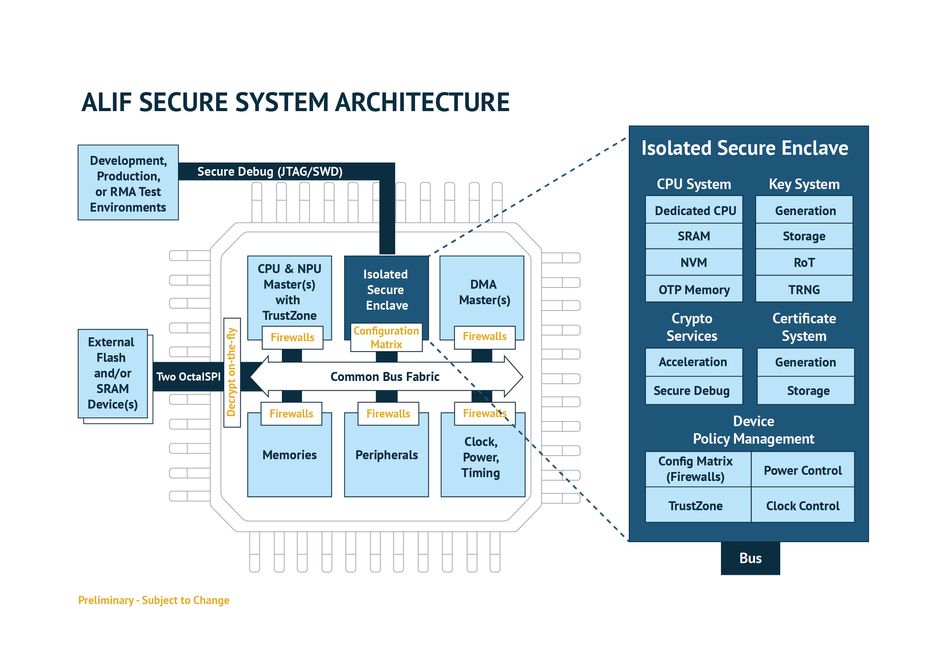
Looking at the security vulnerabilities and security measures mentioned above, we can see the urgency and precedence that embedded security imposes. Security is needed on both the communications and computing levels. That is where multi-layer security can play a central role, and that is what Alif Semiconductor has integrated into their cutting-edge embedded controllers, as seen in their Ensemble™ family.
The Alif Ensemble family of embedded controllers
The Ensemble microcontrollers are scalable and compatible embedded controllers designed for power efficiency, long battery life, and multi-layered security. They provide a strong root of trust, secure device identity, device integrity protection, and secure lifecycle management.
Ensemble’s security features include:
- An isolated security subsystem
- Immutable secure key storage
- Secure cryptographic hardware acceleration
- Secure boot with signature-based code images
- Comprehensive bus fabric firewalls for low-level hardware protection against illegal bus transactions
- Device-wide hypervisor functions to manage security policies, secure software updates, and coordinate device power management
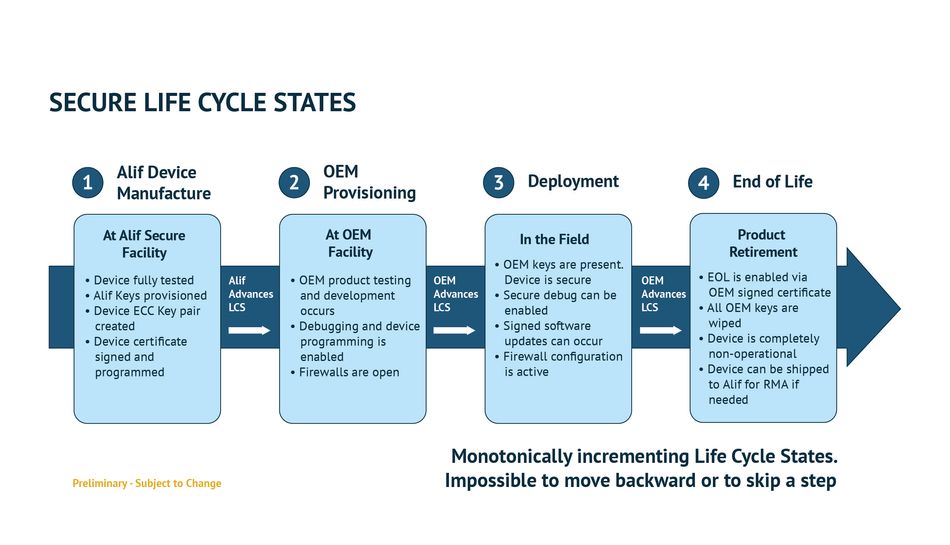
In addition, Alif Semiconductor provides secure management of a device throughout its life cycle from manufacture to deployment, maintenance, and retirement. This ensures Alif’s focus on prioritizing security at every stage of the device’s life cycle.
Security beyond TrustZone
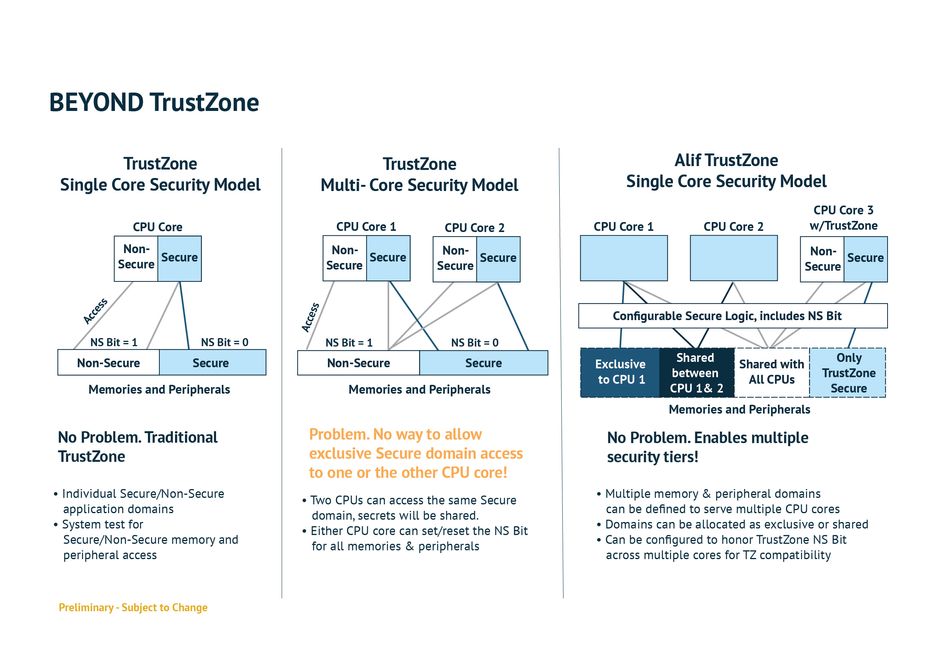
Ensemble’s multi-layered defense provides an extra level of security beyond TrustZone, shielding the device from any potential attack or unauthorized access. As mentioned earlier, TrustZone typically has individual Secure and Non-Secure domains, enabling a trusted execution environment (TEE) for security-sensitive processing. This is what we call a single-core security model.
However, once you go beyond a single core to integrate multiple cores, problems arise. The figure below illustrates that clearly. Two CPU cores accessing the same Secure domain compromise its security, as secret keys and information will be shared.
The solution comes in the form of Alif’s security model. It enables multiple security levels as multiple domains serve more than one CPU core. Domains can be assigned exclusively to specific cores or shared between them. Most importantly, the TrustZone Secure domain remains accessible only to its corresponding core.
The Ensemble family’s multi-layer security, alongside its high computation and ML/AI capability, high-speed connectivity, accelerated graphics, ultra-low power operation, and more, renders it ideal for smart home products, appliances, robotics, point-of-sale, and many more applications.
For more information about the Ensemble processors and microcontrollers, check out the Ensemble™ Family page.
Outlook
Security in embedded systems is becoming increasingly important as their market growth continues to compound. Especially with the emergence of Edge Machine Learning (Edge ML) helping smart devices process data locally, the importance of securing the exchange of data in smart devices is a challenge that will only become increasingly important.
This is the second article in a three-part series examining IoT security problems and solutions as of today. In our next article, we will discuss the need for high security in Edge ML applications and explore the best security solutions for Edge applications.
About the sponsor: Alif Semiconductor
Alif Semiconductor is the industry-leading supplier of the next-generation Ensemble family of 32-bit microcontrollers and fusion processors. Ensemble scales from single core microcontrollers to a new class of multi-core devices, fusion processors, that combine up to two Cortex-M55 MCU cores, up to two Cortex-A32 microprocessor cores capable of running high-level operating systems, and up to two Ethos-U55 microNPUs for AI/ML acceleration. The Alif Ensemble family delivers increased AI/ML efficiency, lowers power consumption, and provides multi-layered security to keep your data safe, all while offering a scalable processor continuum.
References
1. https://www.globenewswire.com/en/news-release/2022/07/20/2483123/0/en/Embedded-Processor-Market-Size-is-projected-to-reach-USD-44-Billion-by-2030-growing-at-a-CAGR-of-8-2-Straits-Research.html
2. https://blackberry.qnx.com/en/ultimate-guides/embedded-system-security#best-practices-for-embedded-security