IoT Platform Security Basics and Essentials
Platform Integrity must be an essential design priority to ensure data protection.

This article is the third article in a four-part series based on the whitepaper by Intrinsic ID that presents an in-depth study of low-cost IoT network attacks and the practical security approaches against them. The first of these articles explores the categories of IoT attacks and their origins. The second goes into the detail of attack surfaces and the mechanisms used to secure the system. This article describes the importance of IoT platform integrity, the components that make up IoT platforms, and highlights the functions of security subsystems at different levels to ensure platform integrity.
Introduction
An IoT platform refers to multi-layer technology that provides a bridge between device sensors and data networks. IoT platforms are among the most pivotal components of an IoT system. These are on-premises software suites and cloud services that facilitate connectivity of network endpoints through monitoring, management, and automation of the connected devices.
Thus, IoT platforms are a set of components that provide infrastructure facilities to the system to manage remote data collection and ensure uninterrupted cross-device communication.
Since these platforms are directly involved with sensor data and have access to communication exchanges within the network, their integrity is critical. Ensuring trust, security, and compliance across the complex platform landscape is essential to engaging the maximum potential of the IoT system.
The following paragraphs detail IoT infrastructure's most significant security component, i.e., a dedicated security subsystem. This module handles most of the security assurance of the IoT platform.
Security Subsystems
A security subsystem (SS) is dedicated hardware within an IC (microcontroller or SoC) that provides services to applications and manages and protects cryptographic assets. It has multiple related IP functions that help maintain platform identity and guard platform integrity.
It stores secret key information and incorporates a hardware engine that uses the stored key to perform high-speed encryption and authentication processing.
Objectives
SS is designed and incorporated into IC to achieve several security functionalities:
- Isolate SS domains from the application domains to protect against software attacks, prevent malicious access, and secure cryptographic keys.
- Secure the data in the system, including information exchanged through data channels and device data stored at endpoints.
- Ensure application security through software integrity measures.
- Secure the software environment through the boot to maintain the confidentiality of network assets
Architecture
Security subsystems in SoC have a specified architecture based upon isolation of the critical network assets from the remaining system. The IoT system is designed as two independent domains: the SS and the application domains.
The application domain is primarily the application environment. It houses public access resources such as input/output interfaces, memory, firmware, controllers, and application software.
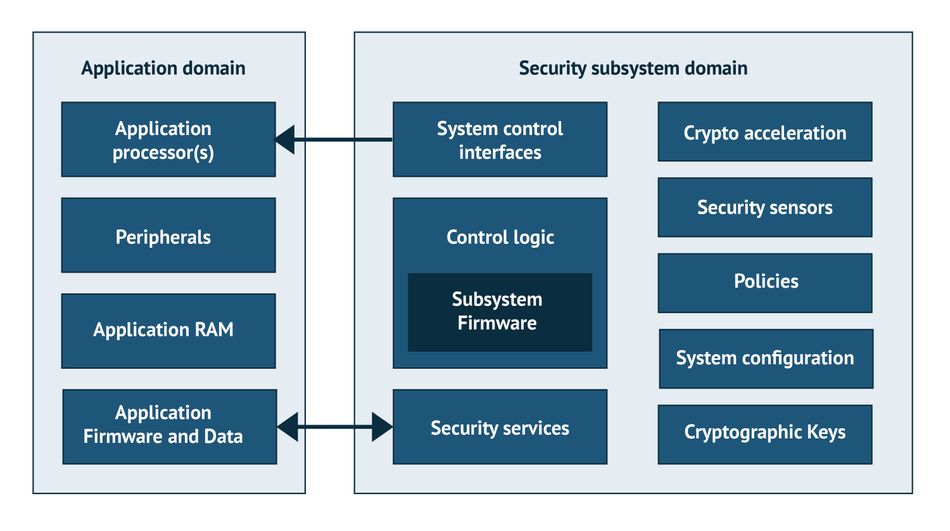
The SS domain houses critical security services that include encryption/decryption mechanisms, cryptographic keys, logic controllers, and security policies.
SSs are integrated into the IC in a modular fashion, in which multiple modules are interconnected to implement various security measures.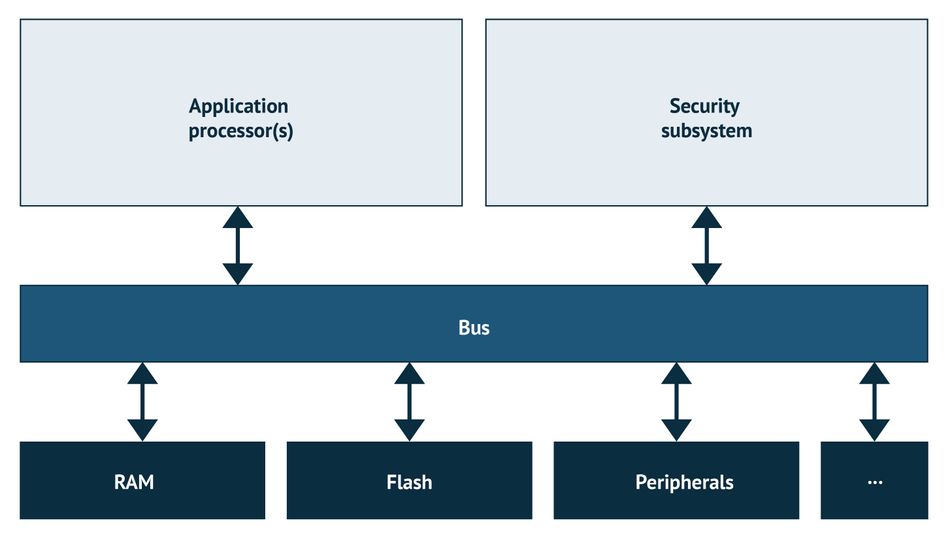
Mechanism
The application environment and the security sub-networks interact with each other through dedicated buses, peripherals, and memory storage devices. When an IC is provided with a power supply, the security subsystem is the first to be powered on. Upon initialization of the SoC, the SS immediately becomes functional and protects the system from attacks during all subsequent activities.
The following lines explore the two common functionalities, i.e., cryptography and secure boot, that SS employs to ensure the IoT platform security.
Cryptographic Keys
Cryptographic keys for encryption and decryption are significant tools for platform integrity. They provide a mechanism for authentication and authorization of system firmware.
Different cryptographic schemes our employed based on the application. These include the signature scheme, which is preferred in environments that cannot be trusted to ensure the confidentiality of the keys. Message authentication schemes are the preferred choice when the latency is a critical parameter to optimize.
The SS domain hosts these cryptographic keys and provides several essential functionalities related to the management and protection of cryptographic keys. These are discussed in the paragraphs to follow:
Key Generation
The cryptographic keys are generated within the security subsystem to maintain confidentiality. A key generator (keygen) generates these by either a Random Number Generator (RNG) or exploiting a Physical Unclonable Function (PUF). The last section of the article contains a detailed description of SRAM PUF developed by Intrinsic ID.
Key Derivation
Key derivation is a cryptographic algorithm that derives one or more cryptographic keys from a secret value such as the main key using a pseudorandom function. Standardized algorithms are employed for derivation to minimize the exposure of the cryptographic key.
Encryption Services
The encryption keys are used to implement encryption and decryption in the network. Application data is ciphered and deciphered to prevent access during data transfer within the network.
Commonly used encryption/decryption schemes include AES-CBC, AES-CCM, RSA, and ECIES.
Data Authentication Services
Cryptographic keys are also employed in a challenge-response handshake to prove one's identity using digital signatures and other verification schemes. These help to maintain the integrity of the software and firmware.
Entity Authentication and Key Agreement Services
Key agreement refers to a protocol whereby involved parties agree on a key such that only they influence the outcome to preclude undesired third parties from forcing a key choice on the agreeing parties.
Entity authentication is also a critical cryptographic service as it allows authentication among different entities. The exchange of keys between a prover and a verifier is used to establish authentication.
Data Attestation
Cryptography also allows SS to verify application data. It ensures data integrity is preserved, indicated by verification indicators from the security system.
Secure boot
Secure boot is an essential mechanism for application protection against tampering with OS files, unauthorized option ROMs, and boot loaders. It is a security standard that ensures a device boot only using trusted software by validating firmware authenticity using cryptographic verification.
The implementation method of secure boot is chosen based on the system's security and latency requirements. It could be either a sequential or a parallel boot.
PUF based Security Solution
Physically unclonable function (PUF) is a technique in hardware security that exploits inherent device variations to produce an unclonable, unique device response to a given input. These variations are deep submicron variations that occur naturally during semiconductor production.
Due to these variations, each transistor in an IC acquires small but measurable differences in terms of electric properties, such as transistor threshold voltages and gain factor. Since these process variations are not fully controllable during manufacturing, these physical device properties cannot be copied or cloned.
Because of these inherent variations, PUFs are very valuable for use as a unique identifier for any given IC. The circuitry within the IC converts the tiny variations into a digital pattern of 0’s and 1’s, which is unique for that specific chip and is repeatable over time. This pattern is a “silicon fingerprint,” comparable to its human biometric counterpart. [3]
This silicon fingerprint is turned into a unique cryptographic key for the individual chip. This key protects the device's application keys and certificates and is used as the “root of trust” for security.
There are multiple techniques for using PUF technology to secure the hardware and communications, including Metal resistance PUF, Delay PUF, Digital PUF, Optical PUF, Magnetic PUF, DRAM PUF, etc.
SRAM PUF from Intrinsic ID
The following lines explore the data security and authentication solution, SRAM PUF, created by Intrinsic ID. Intrinsic ID SRAM PUF is based on the behaviour of standard SRAM memory, available in any digital chip. Every SRAM cell has its preferred state every time the SRAM is powered, resulting from random differences in the transistor threshold voltages. Hence, while powering SRAM memories, each memory will yield a unique and random pattern of 0s and 1s, which is a fingerprint unique to that SRAM.
However, this SRAM PUF fingerprint is “noisy,” and turning it into a high-quality and secure cryptographic key requires further processing.
Using the “Fuzzy Extractor” IP makes it possible to reconstruct the same cryptographic key every time and under all environmental circumstances.
The secret key is not stored but is dynamically regenerated from the SRAM PUF inside a secure perimeter. This means no key is stored there, so it can’t be stolen or compromised even if the memory is breached. Thus, IoT devices and networks are completely secure from intruders.
Conclusion
Any SoC must be designed with security as a top priority. Platform integrity is highly focused during both architectural design and system flow. The article provided an overview of how these system-on-chips and other ICs implement strong security and platform integrity through on-chip integrated security subsystems. These carry out validation, verification, and authentication of firmware, software, and application data through cryptographic keys and mechanisms and secure boot implementation.
This article is an excerpt from the whitepaper, Preventing a $500 Attack Destroying Your IoT Devices. Learn more about how to equip yourself with the essential knowledge needed to secure your IoT networks and prevent attacks and security breaches by downloading the paper now.
Download the free whitepaper here.
About the sponsor: Intrinsic ID
Intrinsic ID is among the world’s leading providers of security IP for embedded systems based on physical unclonable function or PUF technology. The technology provides an additional level of hardware security utilizing the inherent uniqueness in each and every silicon chip. The IP can be delivered in hardware or software and can be applied easily to almost any chip – from tiny microcontrollers to high-performance FPGAs – and at any stage of a product’s lifecycle. It is used as a hardware root of trust to validate payment systems, secure connectivity, authenticate sensors, and protect sensitive government and military data and systems. Intrinsic ID security has been deployed and proven in millions of devices certified by EMVCo, Visa, CC EAL6+, PSA, ioXt, and governments across the globe.
References
1. https://docs.microsoft.com/en-us/windows-hardware/design/device-experiences/oem-secure-boot
2. Echard C. Ensuring Software Integrity in IoT Devices. Journal of Information Technology & SoftwareEngineering. 2017 Jan 1;07.
3. How Physical Unclonable Functions (PUFs) are Creating Trust (wevolver.com)

