A Device-Unique Fort Knox: Building a Key Vault for IoT Application Keys
Secure key storage is essential for internet-of-things (IoT) devices. Most IoT devices utilize multiple application-specific keys from diverse suppliers to enable applications such as authentication, message encryption, software/firmware encryption, to name just a few.

Image rights: Pixabay
This article was first published on
www.intrinsic-id.comEach application requires a different key in order to maintain separation so that even if one key is compromised, the other keys remain secure. To secure all of these keys, IoT devices need a key vault: a device-unique Fort Knox of sorts to provide not only secure storage, but also secure transit in and out of the vault. A key vault provides a foundation of security on which higher-level services and applications can be built.
Non-volatile memory (NVM), such as flash, and fuses (or e-fuses) are commonly used to store cryptographic keys. Fuses are generally considered more secure than flash, however, they are also less flexible, as they are a one-time programmable (OTP) solution. The biggest issue is that both approaches rely on storing key material in the plain at some location on the chip, leaving them vulnerable to attacks.
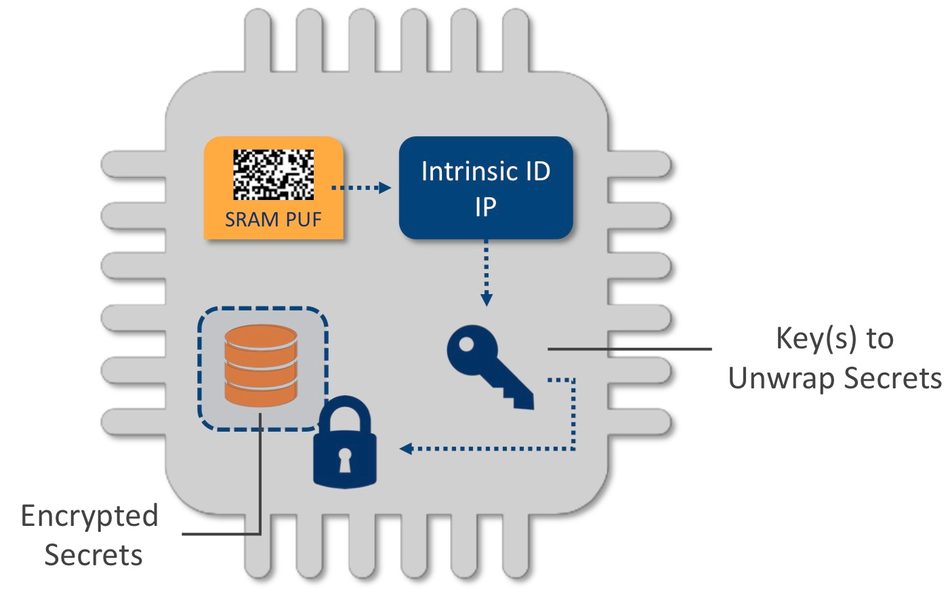
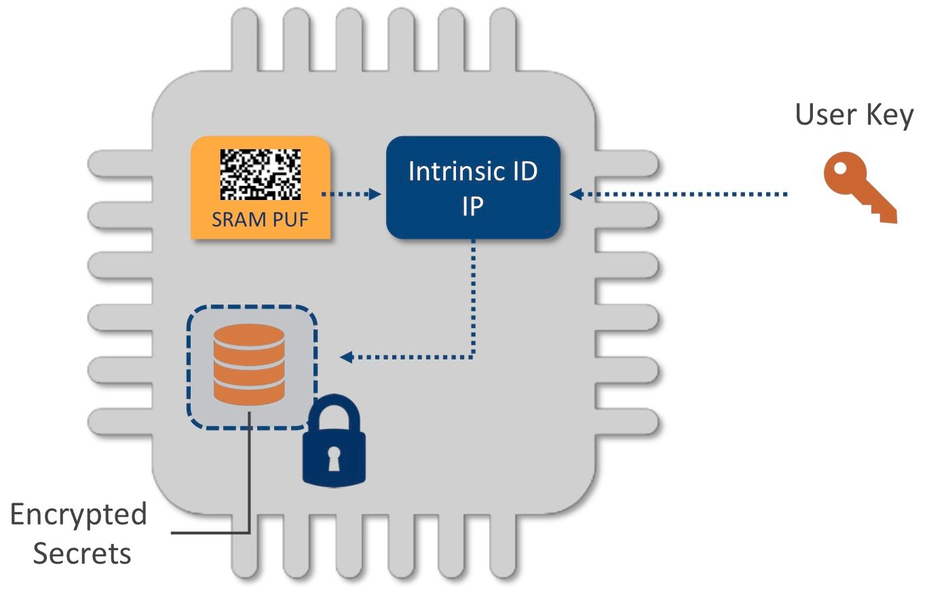
Using a device-unique characteristic, such as a physical unclonable function (PUF), to create a root-of-trust for a device provides unique advantages in terms of security, cost, flexibility, and easy integration. Most importantly, with PUFs, plain key material is never stored on the chip, so there is nothing for attackers to find.
QuiddiKey, the Intrinsic ID SRAM PUF-based key-management hardware IP, provides a root-of-trust for building a secure key vault. This root key is never stored, but rather reconstructed from the device physics whenever it is needed. QuiddiKey enables application keys to be wrapped by cryptographic keys that are generated from the root key, according to application-specific requirements, so they are protected based on silicon-specific properties that are extremely hard to reverse-engineer. QuiddiKey also enables keys that have been unwrapped for application access to be output through a dedicated secure output interface that is connected to the device’s crypto module, so they are never visible at the registers.
QuiddiKey hardware IP is shipped with a driver API to make access to the commands needed to create application key vaults smooth and easy. Intrinsic ID recently published a new application note that guides users through the process of creating a key vault for a device containing the QuiddiKey hardware IP, using the QuiddiKey API driver. The application note includes generic example of the driver API commands and code samples for wrapping, storing, unwrapping, and outputting application keys.
To learn how to use QuiddiKey to build your own device-unique Fort Knox for application keys, you can access the application note here.