How to Get Started on Building Trust in Your Chips? Use QuiddiKey!
To secure the billions of devices that are being connected to the Internet of Things, every device needs to have the capability to protect sensitive data and secure communications.
This article was first published on
www.intrinsic-id.comOn many occasions, Intrinsic ID has described how Physical Unclonable Functions (PUFs) are used to create and protect a strong cryptographic root key, such as in its white paper “SRAM PUF: The Secure Silicon Fingerprint.” However, a PUF as such only gets you so far. To actually secure the billions of devices that are being connected to the Internet of Things (IoT), every device needs to have the capability to protect sensitive data and secure communications. This is where the Intrinsic ID hardware IP product QuiddiKey® comes in.
Creating a Strong Root Key
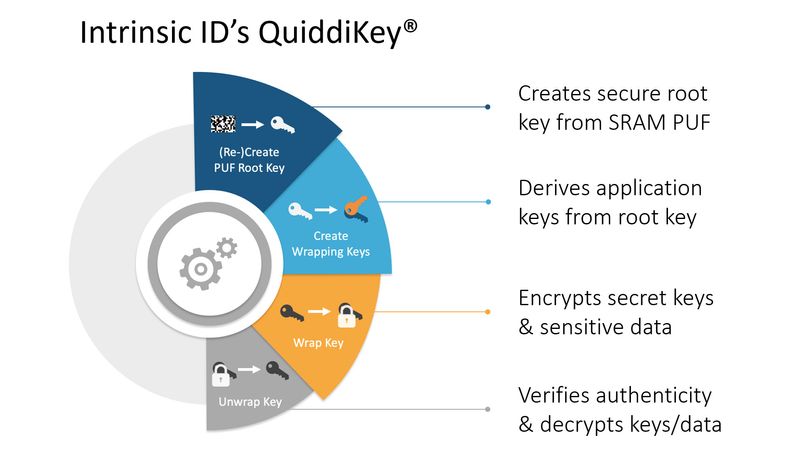
The fundamental first step that QuiddiKey takes is to create a high-quality and secure cryptographic root key from tiny variations in the silicon of chips, which are device-unique and remain stable at every device startup and under all environmental circumstances. Deriving a root key with QuiddiKey has great security advantages compared to traditional key storage in non-volatile memory. Because the key is never permanently stored, it is not present when the device is not active (no key at rest), and hence cannot be found by an attacker who opens up the device and compromises the memory contents.
Deriving Multiple Keys
However, having a strong root key alone is not enough. Any security system typically requires more than a single cryptographic key. This is because:
- different algorithms expect keys with different lengths or different structures.
- different applications require secrets with different lifetimes.
- different users of a system typically need their own keys for authentication.
- if one key gets compromised, this should not affect the security of other secrets.
For these and other reasons, it is a well-established best practice in security design to use a single key only for a single purpose and/or a single application. To meet the single-key/single-use requirement, a key management component with the ability to generate multiple application keys from the previously described, strong root key should be used.
To make it easier for designers of the security architecture of a chip, Intrinsic ID has recently published the application note “Multiple Key Generation with QuiddiKey.” This application note describes in detail how one can use the secure key derivation functionality of QuiddiKey to derive multiple, cryptographically separated application keys from a single root key. Being cryptographically separated means they are generated in such a way that the disclosure of a particular derived key does not affect the security strength of any other derived key.
Building an Embedded Key Vault
Now that a chip has all required keys for a strong security system, how can one guarantee that all these keys are protected? This guarantee comes from utilizing the root key derived by QuiddiKey for creating an embedded key vault to protect all secret data on a device.
By encrypting all keys (and other sensitive data for that matter) on a chip with the root key or a key derived from the root key – neither of which is ever stored on the device – a key vault is created with the following properties:
- Like the root key, no other key is ever stored in the plain
- Different applications can store and use their own unique keys
- Key vault output can be sent directly to the hardware crypto engine
Intrinsic ID created another application note to help designers to implement this embedded vault, “QuiddiKey Use Case: Embedded Key Vault.” Implementing this embedded vault ensures that all keys and sensitive data on a chip are stored with the same level of protection as the root key from QuiddiKey.
Getting Started with QuiddiKey
Now that all steps of how to design a secure system based on SRAM PUFs have been described, there is only one thing missing. How can you get started working with a hardware IP block such as QuiddiKey? What everybody designing chips knows is that the design has to be “first time right.” There is no margin for error, as hardware cannot be changed once it is in production. This is why Intrinsic ID knows it is important for hardware engineers to get familiar with an IP block before integrating it into their design.
For this purpose, QuiddiKey can now also be integrated on a Digilent Arty Z7-20 board in order for engineers to get a feel for the IP block, its functionality, interfaces, and integration flow. This way, anyone can get familiar with the QuiddiKey hardware IP before including it into the actual targeted chip design. And to support this effort, Intrinsic ID now also has the application note “Getting Started with QuiddiKey” available. This document walks you through the general integration flow step-by-step and answers the most important integration questions.
By combining this most recent application note to get engineers started on integrating QuiddiKey with the documents describing key derivation and creating an embedded vault, Intrinsic ID has a complete library to offer anyone who wants to get started with building a security architecture for a chip, based on SRAM PUF technology. So, no need to hesitate! Download these application notes and start designing your system today.