IoT needs trust: The current state of IoT security
Trustworthy and reliable applications are fueling the worldwide IoT success story. This article explains why protecting IoT edge devices is crucial in an environment with threats on the rise.
This is the first article in a 3-part series that explains the current state of IoT security and introduces cutting-edge, highly secure MCUs from Alif SemiconductorTM.
The Internet of Things (IoT) already plays a massive part in our everyday lives – whether at work, at home or in public environments. We are constantly interacting with connected smart devices that are seamlessly integrated into our everyday lives. IoT is an interconnected system of physical devices that work and exchange data digitally with one another via sensors, actuators, processors, and software technologies. IoT has provided us with accessibility and the ability to realize ideas that were difficult or even impossible before. However, with every advance in technology comes a new set of challenges and risks. Identifying and managing those risks is fundamental as we continue to embrace IoT in our daily lives.
Arguably the most crucial aspect of IoT to consider today is security, with some of the most critical threats including:
- Unencrypted data storage
- Unsecured financial information
- Unauthorized access to physical property
- Weak passwords and ID verifications
- Malicious IoT devices (commonly known as Botnets)
In the first half of 2021 alone, cyberattacks against IoT devices more than doubled to reach a whopping 1.5 billion attacks. With the increasing rate of security threats, the prioritization of research and efforts to curtail online attacks is also on the rise, leading to major breakthroughs in IoT security.
In addition, national governments have started legal initiatives to educate people on the risks of cyberattacks and drive the industry to secure IoT ecosystems. For this purpose, regulations aim to standardize assessing risk and certifying IoT products for public use.
Risk Assessment, Vulnerabilities, and Countermeasures
IoT security is a latent value rather than a typical product feature. However, it is a prerequisite for trusted and reliable IoT services. IoT product requirements are built based on the outcome of a proper risk assessment. For this purpose, target use cases should be carefully reviewed before product development to identify potential threats and attack scenarios in order to implement appropriate countermeasures. Attempting to add security features at the end of the design phase or to previously existing designs will leave gaps susceptible to attack.
In general, attackers target and exploit the availability, confidentiality, or integrity of an IoT ecosystem. For example, a common target for hacking attempts is IoT metering devices located in private environments (e.g., IoT-based utility meters in households). These devices report billable consumption data that an attacker can exploit.
Another example is the security risk of unauthorized access to healthcare devices. Whether it is access to an organization’s IT infrastructure or medical data, gaining control of medical IoT devices may allow for dangerous tampering with a device’s functionalities, which may result in threatening and fatal consequences.
Similarly, cyberattacks on IoT systems of commercial businesses can create a devastating financial loss. A forced failure of installed IoT devices or information theft can sabotage the company’s reputation or cause a loss in market share.
The motivation behind IoT cyberattacks and hacking scenarios may differ on a case-to-case basis. That is why it is strongly recommended that IoT manufacturers proactively implement countermeasures to avoid public disputes about a potential lack of security.
Securing the software is a critical aspect, and it boils down to large-scale monitoring of behavior to identify suspicious activities that indicate illegal conduct or infringement. However, as Lin Nease, Chief Technologist for IoT at HPE, described in an interview, hardware security is more of a “keep bad things from happening in the first place” approach.
Securing hardware enables identity verification of two endpoints and encryption-based protection of the exchanged data between them. In other words, it helps establish a degree of trust between two devices in which both endpoints can clearly identify one another. This is commonly referred to as a root of trust (RoT). This security measure primarily blocks attackers from hacking or accessing the system.
You may look at the hardware vs software comparison as a preventive vs reactive security approach. Hardware security is more preventive, focusing on establishing a healthy, secure system in the first place. Software security is reactive, with a focus on reacting to identified potential threats. Nevertheless, it is always a matter of combining hardware and software security approaches in a way that fits the application at hand. Your goals and needs will determine how you balance your security methods.
If you are designing an IoT product, keep in mind that secure hardware helps protect the device itself and the network to which it is connected. It gives you the precise ability to control which devices communicate with one another and how.
IoT Endpoint Security
For the design of a new IoT device, three aspects predetermine the selection and strength of your countermeasures:
- Expectable threat scenarios
- Attacker capabilities (skills/equipment)
- Assigned IoT security budget
There is no doubt that cryptography-backed methods, such as data cyphering and digital signatures, combined with smart approaches for key generation and key management, are efficient countermeasures against most cyberattacks. But cryptographic keys are, by nature, extremely vulnerable to eavesdropping, even if they are temporarily used.
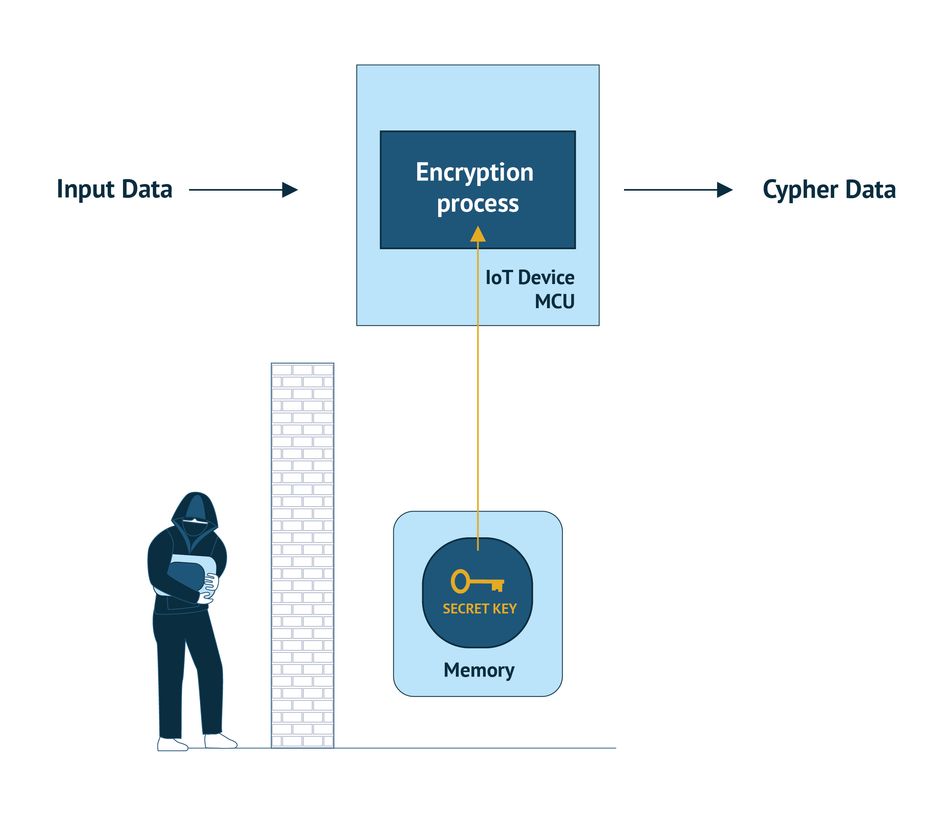
Look at Figure 1, for example. To have secure IoT business models, strong device authentication is required. That means IoT devices must be clearly identified and verified. That’s where a unique secret key comes into play. The secret key is a string of characters in an encryption algorithm that is assigned to the device by a trusted third party and injected into the device’s local memory, usually during production. [AK1] [2] That is why attackers tend to eavesdrop or listen passively to network communications as they seek access to private information, such as secret keys, memory content, or sensitive data – otherwise known as an eavesdropping attack.
Simply put, eavesdropping attacks do not require the attacker to seek that information actively. They can merely develop a piece of software that sits somewhere in the compromised device or along its network path and captures all the pertinent data to be analyzed later.
For that reason, the design of a secure IoT device must protect all access paths that an attacker might try to exploit, including the memory content and internal data connection to the microcontroller unit (MCU). Assigning a strong countermeasure can overburden a potential attacker to an extent beyond their skills or equipment capabilities, preventing them from accessing the device.
Security is increasingly becoming a top priority for IoT systems. From establishing a root of trust to utilizing encryption algorithms to protect sensitive data, including identity keys, certificates, and secure booting, maintaining a high level of hardware and software security is crucial for designing secure IoT solutions.
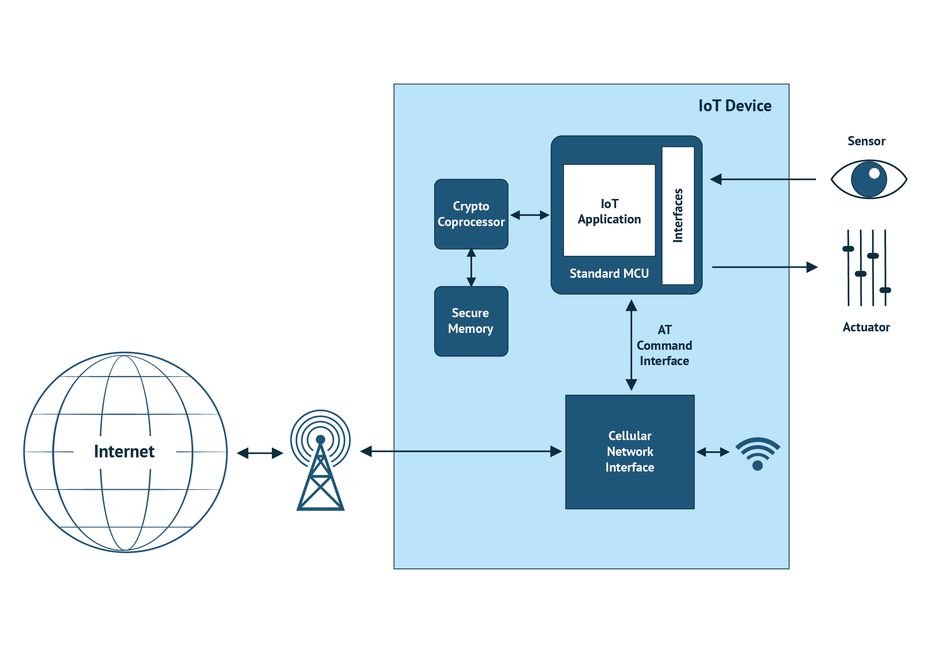
Figure 2 shows an example of how a cellular IoT device can ensure the security of its data by integrating a crypto coprocessor between the MCU and the memory. This protects against unauthorized access to the secure memory, including eavesdropping and malicious tampering. Recently, cutting-edge microcontrollers have rebuilt the security of IoT devices with integrated, multi-layer security systems, offering device integrity protection, secure identity, and a strong hardware RoT. This secure architecture ensures a protected ecosystem for promising technologies like edge AI/ML. One example is Alif Semiconductor’s family of highly scalable embedded processors, which can prevent rogue software attacks and add more security beyond TrustZone (system-wide security).
Outlook
To reduce IoT vulnerabilities and provide out-of-the-box secure device designs, new system-on-chip IoT solutions integrate all involved functional elements on a single chip. At the same time, a unique device identity and a root of trust are provided in a secure environment that prevents any logical or physical intrusion and protects against the tracing of internal data traffic.
This is the first article in a three-part series examining IoT security problems and solutions as of today. Our next article will provide a technical introduction to Alif Semiconductor products and explore why this technology represents a new generation of highly integrated, secure MCUs, efficiently supporting the design of secure application-specific IoT endpoint devices.
This article and illustrations was contributed to by Kersten Heins.
About the sponsor: Alif Semiconductor
Alif Semiconductor is the industry-leading supplier of the next-generation Ensemble family of 32-bit microcontrollers and fusion processors. Ensemble scales from single core microcontrollers to a new class of multi-core devices, fusion processors, that combine up to two Cortex-M55 MCU cores, up to two Cortex-A32 microprocessor cores capable of running high-level operating systems, and up to two Ethos-U55 microNPUs for AI/ML acceleration. The Alif Ensemble family delivers increased AI/ML efficiency, lowers power consumption, and provides multi-layered security to keep your data safe, all while offering a scalable processor continuum.


