The Rise in Automotive Electronic Controls Prompts Cybersecurity Concerns
With some modern vehicles having more than 100 electronic control units, along with the rise of wired and wireless communication protocols, automotive cybersecurity is now a critical concern.
This is the second article in a 5-part series exploring the future of mobility. The series looks into which technologies enable rapid advancements in the efficiency, safety, and power of the vehicles of tomorrow. The series looks into which technologies are enabling the necessary rapid advancements in efficiency, safety, and power. This series is sponsored by Mouser Electronics, an online distributor of electronic components. Through their sponsorship, Mouser Electronics is dedicated to supporting a future of connected and efficient mobility.
Robust Automobile Safety, Security, Reliability
About 95% of road accidents occur because of human errors.[1] In the U.S. alone, these accidents result in more than 50 million serious injuries and a cost of over $3 trillion (USD) every year. Adding to this, autonomous vehicles increasingly require more complex systems and components which pose an increasing risk to the safety and enjoyment of drivers.
For an automobile to be robust, it must have:
Safety: specify that an automobile should not harm any other agent in its environment because of hazards caused by malfunctioning electrical/electronic (E/E) components.
Security: the requirement that ensures the car’s electronic components must be resilient against system hackers.
Reliability: Refers to the robustness of electromechanical and mechanical components and their interfaces with the E/E components of the system.
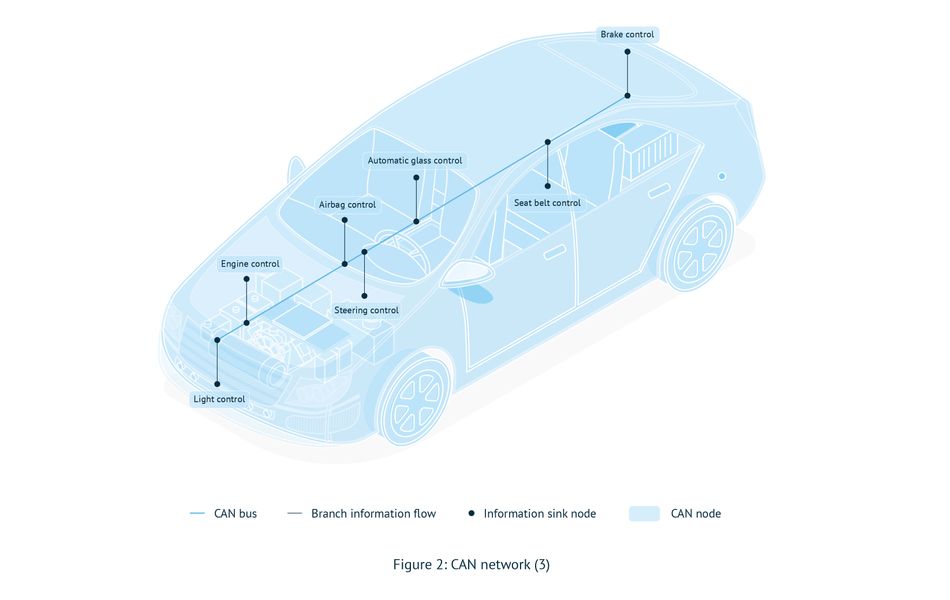
The embedded systems in an automobile are composed of more than 100 ECUs connected utilizing a controller area network (CAN) protocol as seen in Figure 1. Such systems have more than 100MB of software that is expanding connectivity to clouds and other internet services, handling an ever-growing volume of digital information, and have highly vulnerable points, with a mix of various sensors and actuators. Consequently, this can lead to possible dangerous automotive safety situations that result from cyberattacks.
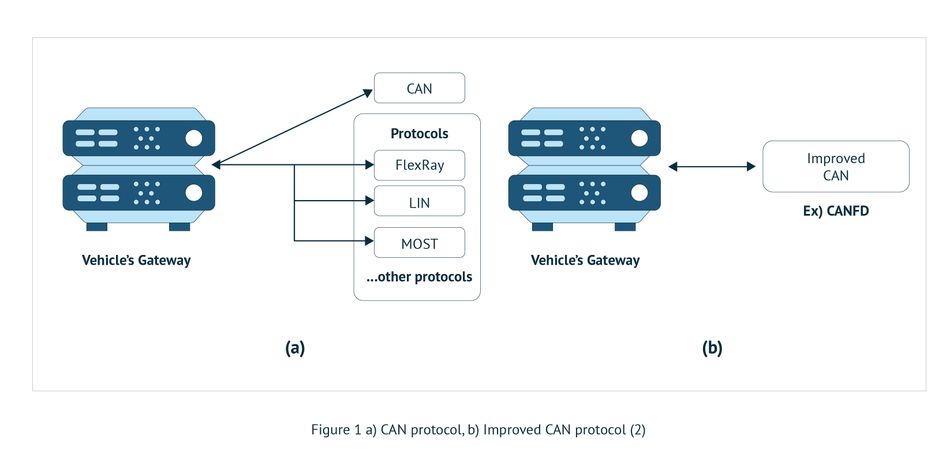
The most often-used information technology (IT) configuration is a periodic activation of tasks that get executed by ECUs along with messages that are coupled with run-time priority-based scheduling transmitted by the CAN bus.
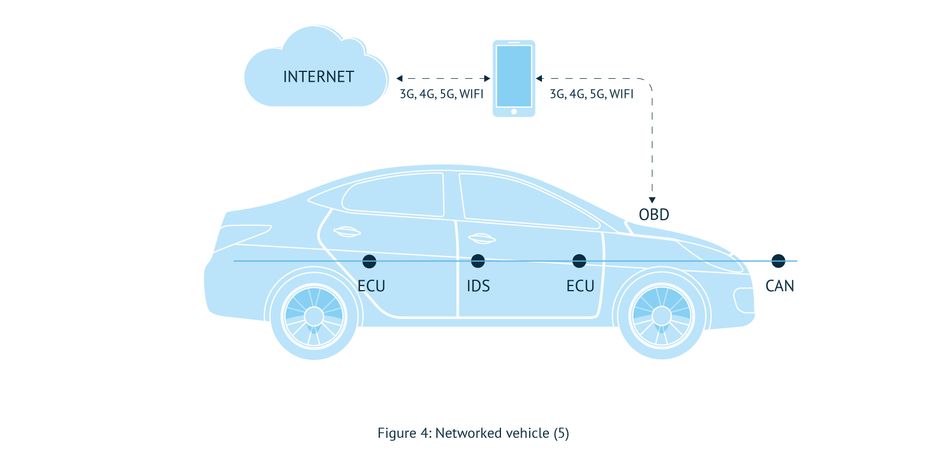
Such things as raising the radio volume are just nuisances to the driver and passengers, but think of the hacker remotely stopping a vehicle on the road or increasing the speed of the vehicle, which will endanger the lives of the driver and passengers.
General Security-Risk Analysis (SRA)
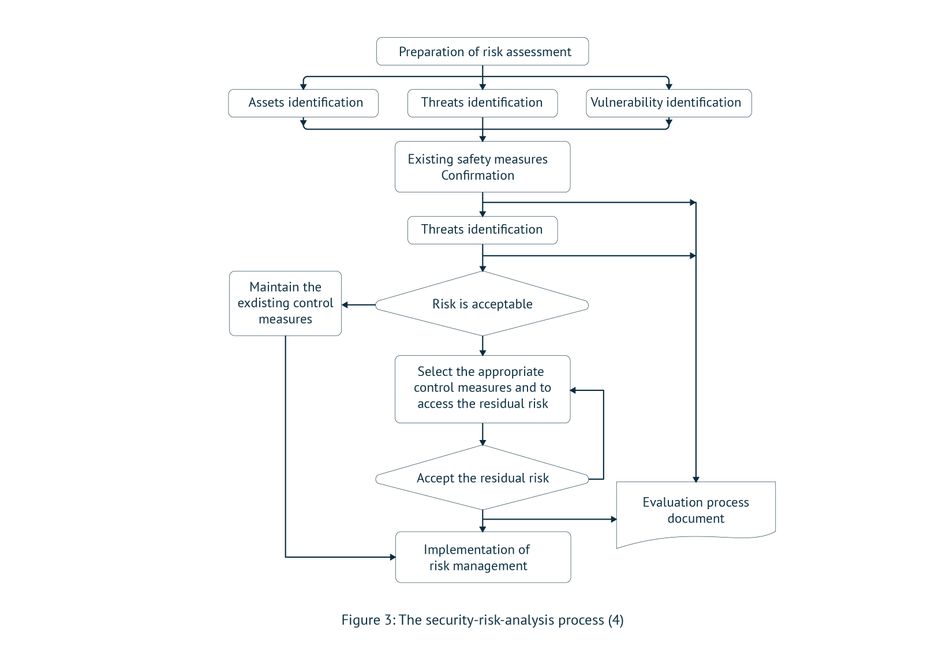
Designing, developing, and deploying information security methods for vehicles requires a systematic security risk assessment and management process throughout the vehicle’s lifecycle. A security risk analysis (SRA) should be performed with a thorough analysis of cyber threats for new automotive vehicles to achieve this.
SRA is a methodology that estimates the risk and possible damage to assets. It determines the level of risk-based upon attack potential of threats and potential damage if assets are compromised. The security of targeted assets is ensured by an appropriate risk management algorithm, which results from SRA, which consists of processes as described in Figure 3.
A Cyber kill chain is a process of analyzing cyberattacks to identify threats to the organization at each stage of the attack, eliminating or mitigating the attacker’s purpose, and then planning and implementing measures that will secure the organization's system.
Security Access in Automotive Diagnostic Communication
Automotive systems have experienced many documented cases of attacks in recent times. Numerous areas might also act as a stepping-stone for such attacks. Among these are the automobile controller area network (CAN), hackers using IT-based communication remotely, and attacks using servers and smartphones.
The vehicle’s CAN network is a prime target to access the automobile’s diagnostic functions. Vehicle diagnostic functions will write to the vehicle’s internal memory and protect access to crucial functions, such as reprogramming routine processing and security access services (Figure 3). These are usually built into many ECUs and linked to intrusion detection systems (IDS). The problem is that this effort is not good enough by itself to keep out the creative innovations of smart hackers who can input new commands into the On-Board Unit (OBD).
Security evaluations of ECU software update communication processes. However, many automaker’s ECUs contained defects in implementing their security access services, enabling brute force attacks or man-in-the-middle attacks via diagnostic tools.
Improved methods need to be implemented. As hackers get more creative, the automobile industry needs to get even more creative in defending automobile system attacks.
ECUs Vulnerable to Security Attacks
No longer are automobiles a fully mechanical system. They are becoming wirelessly connected computers on wheels. One major effort to combat hackers is the United Nations Economic Commission for Europe (UNECE) WP29 Working Party on Automated/Autonomous and Connected Vehicles (GRVA). This group has begun a task force on cybersecurity and software updates (CS/OTA).
This task force has developed and delivered a recommendation for integrating regulations on cybersecurity and software updates for vehicles.
Vehicle manufacturers will have to ensure that suppliers and service providers implement a cybersecurity management system (CSMS). The processes have to include development, production, and post-production and consider the monitoring of risks and threats to the vehicle and incident response processes.
Over-the Air-Update Security
To date, over-the-air (OTA) software updates for automobiles can be exploited by hackers to compromise vehicle security and safety. This issue has not yet been covered extensively enough.
The latest automobiles are quite vulnerable to cybersecurity attacks because of the computing and internet connectivity embedded within the vehicle system. The industry must protect the vehicle, driver, and passengers by implementing effective testing to detect software flaws and weaknesses. Regular updates need to be routine with critical security patches, fixes for bugs, and other needed enhancements. Just as our computers need these security measures, the latest vehicles need them even more because hacks can lead to accidents, injuries, and even deaths on the roads. OTA software is presently the most convenient, efficient, and cost-effective means to deliver software updates—just ask Tesla Inc.
Microchip delivers security solutions
Microchip has the first automotive cryptographic companion security IC, the TrustAnchor100 (TA100) CryptoAutomotive™ security integrated circuit that provides a means to implement security into existing systems without costly redesigns. The IC provides external Hardware Security Module (HSM) support for secure boot, CAN message authentication, Electric Vehicle (EV) battery authentication, Transport Layer Security (TLS), Wireless Power Consortium (WPC) 1.3 Qi® authentication, High-Bandwidth Digital Content Protection (HDCP) and more.
Multiple OEMs worldwide would approve the TA100 as a solution for E-safety Vehicle Intrusion Protected Applications (EVITA) Medium and EVITA Full HSM requirements.
Microchip TA100 provides this security with CAN Message Authorization. Vehicle diagnostic functions will write to the vehicle’s internal memory and protect access to crucial functions, such as reprogramming routine processing and security access services.
Microchip’s TA100 provides the following:
Full and Partial Secure Boot
Secure Firmware Update
CAN Message Authentication
WPC 1.3 Qi High-Power Transmitter Authentication
High-Bandwidth Digital Content Protection (HDCP) Cryptographic Support
Network Authentication and Session Establishment using TLS
Electric Vehicle (EV) Battery Authentication
An ongoing test phase is in progress. Combining the TA100 and an integrated software stack will provide production-ready software for automotive Tier 1 and original equipment manufacturers (OEMs), enabling them to easily add security to any automotive module. Essentially, in addition to the TA100, the automotive community needs to find/groom the most creative and talented hackers in the industry as the White Hats who will thwart the efforts of the Black Hats.
Conclusion
With the modernization and automation of cars and other automotive vehicles, threads are not exclusively to safety issues caused by human error. Cyberattacks are an increasing concern for automakers who need to provide systems capable to prevent any damages to the vehicle and therefore to the driver and other passengers. Hackers as well as automobile technology are learning to intrude into vehicle systems. A possible solution are CSMSs systems which are a tool to decrease such risks of breaches in cybersecurity. Connectivity is bringing easiness to the driving experience but the safety and security of vehicles and humans cannot be compromised with the introduction of these advances.
This article was initially published by Mouser and Microchip in an e-magazine. It has been substantially edited by the Wevolver team and engineer Nicolas Sarmiento Sierra. It's the second article of a 5-part series exploring the technologies that enable the future of mobility. Future articles will examine the cybersecurity concerns in connected vehicles, discuss solutions for fast charging, and dive into how ethernet can deliver optimum data networks.
The first article looked at software control.
About the sponsor: Mouser
Mouser Electronics is a worldwide leading authorized distributor of semiconductors and electronic components for over 1,100 manufacturer brands. They specialize in the rapid introduction of new products and technologies for design engineers and buyers. Their extensive product offering includes semiconductors, interconnects, passives, and electromechanical components.
References
1. Parliament E. Road fatality statistics in the EU (infographic) [Internet]. 2020 [cited 2021 Jun 21]. Available from: https://www.europarl.europa.eu/news/en/headlines/society/20190410STO36615/road-fatality-statistics-in-the-eu-infographic
2. Jeong YN, Son SR, Jeong EH, Lee BK. An integrated self-diagnosis system for an autonomous vehicle based on an IoT Gateway and Deep Learning. Appl Sci. 2018;8(7):1–24.
3. Zhou A, Li Z, Shen Y. Anomaly detection of CAN bus messages using a deep neural network for autonomous vehicles. Appl Sci. 2019;9(15):1–12.
4. Chang Lee M-. Information Security Risk Analysis Methods and Research Trends: AHP and Fuzzy Comprehensive Method. Int J Comput Sci Inf Technol. 2014;6(1):29–45.
5. Zhang J, Li F, Zhang H, Li R, Li Y. Intrusion detection system using deep learning for in-vehicle security. Ad Hoc Networks [Internet]. 2019;95:101974. Available from: https://doi.org/10.1016/j.adhoc.2019.101974
About Mouser Electronics
Mouser Electronics is a worldwide leading authorized distributor of semiconductors and electronic components for over 1200 industry-leading manufacturers. We specialize in the rapid introduction of...
202 Posts